Windows 10’s new feature wants you to create a Microsoft account; ditch local accounts
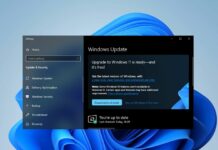
If you're using a local account on your PC, you may receive a prompt to create a Microsoft account. This feature will be enabled by default in the May 2024 Patch Tuesday update for Windows 10. The update will be available to both the general public and IT admins on May 14.
Microsoft says it accidentally added Copilot app to Windows Server 2022
Microsoft is forcibly installing Copilot on Windows machines, and Windows Server 2022 is the latest target. Previously, the Copilot app appeared in Windows Server 2025 builds and completely vanished after a few days.
Windows 10 KB5036892 out with desktop features (direct download links)
Windows 10 KB5036892 is now available for everyone, and it has some new features, such as Bing Spotlight integration on the desktop. This Patch Tuesday security update can be installed via...
Windows 10 KB5034441 0x80070643 not fixed even after three months
Users have reported that after three months of release, updates like Windows 10 KB5034441 have failed due to 0x80070643. This update is mandatory, as it is meant to patch recovery partition security issues on Windows 10. However, many users are unable to install it.
Microsoft clarifies Windows 10 paid update for consumers will be revealed later
Windows 10 will no longer receive support after October 14, 2025. However, you can extend the support by paying an annual fee. Microsoft has provided details about the extended updates for Windows 10, which could cost up to $61 for enterprises.
Windows 10 KB5035941 out with features (direct download)
Windows 10 March optional update comes with several new features, including MSN on the lock screen. This update can be accessed via Windows Update, but Microsoft has also provided direct download links for the Windows 10 version 21H1 offline installer on the Microsoft Update Catalog.
Microsoft is adding MSN features to Windows 10 lock screen
Microsoft had shifted its focus to Windows 11, and Windows 10 was expected to be put on the back burner. However, in recent months, Windows 10 received several new features. Today, Microsoft is introducing MSN cards to the lock screen.
Microsoft says uninstalling Copilot in Windows 10 isn’t supported for now
There's no way to uninstall Copilot in Windows 10, at least for now. But there are a couple of workarounds you can apply so that it doesn't pop up even when pressing its shortcut key.
Windows 11’s speech recognition gets axed in six months, but it’ll work on Windows...
The new Voice Access app will replace the WSR app from September 2024 on Windows 11 22H2 and newer versions. But Windows 10 22H2 and Windows 11 21H2 users can continue using WSR.
KB5035849 fails with 0xd0000034, but there’s a fix for Windows 10 and Server users
Some users have reported that KB5035849 update for Windows 10 and Windows Server is failing with error code 0xd0000034. However, there is a quick fix for this issue. You can go to the Microsoft Update Catalog and manually install the patch using the .msu installers.