A recent issue, which is not widespread, means some users will encounter this frustrating scenario: Remote Desktop Protocol (RDP) refuses to accept Microsoft Account (MSA) credentials, even when correct details are provided.
If you’re affected, you might see an error “Your credentials did not work: The credentials there were used to connect to [network name] did not work. Please enter new credentials.”
This issue may arise from a range of technical factors. Some are easy to address, while others require more nuanced troubleshooting. Some may even require intervention from Microsoft itself, or third-party software and service providers.
Why is RDP rejecting Microsoft account logins with the “Your credentials did not work” error?
As I recall my own experiences, and research problems with Remote Desktop Connection logins – and their solutions – I see four common causes:
- Credential Validation Fails: The operating system may be unable to confirm the authenticity of MSA logins. This is a frequent issue, and happens to me pretty regularly. Unfortunately, it’s not always something end users can resolve on their own. This process requires interacting with Microsoft servers over the Internet, and is therefore subject to a range of possible gotchas (some mentioned below, others tied to possible issues with connectivity, DNS, or network protocol problems).
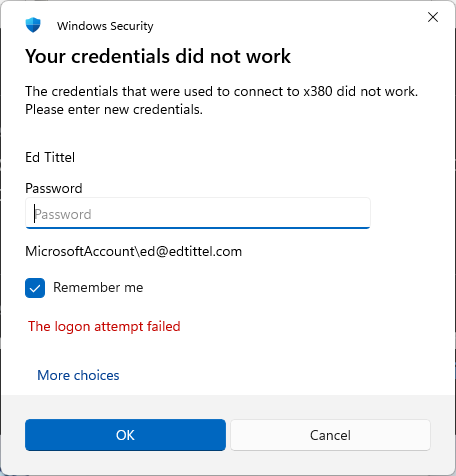
- Problems with Secure Channel Negotiation: RDP relies on secure channels to exchange credentials. If this handshake process fails, authentication will not proceed. It’s hard to distinguish this failure from the preceding one.
- Time Synchronization or DNS Resolution Issues: A mismatch in system clocks or DNS lookup failures can disrupt credential verification. Ensuring that the system’s date and time are accurate (via Settings > Time & Language > Date & time > Sync now) and changing DNS settings (especially if using manual configuration, not DHCP) can sometimes resolve the problem.
- Misconfigured Credential Policies: Group policy or local security policy misconfigurations may block MSA logins over RDP. To learn more about potential gotchas, dig into this MS Learn guide Configure Security Policy Settings.
I investigated potential RDP and MSA login conflicts
Beyond the basic and most common issues identified in the preceding section, other factors sometimes play into RDP connection problems.
These may require digging into account set-up and requirements for “problem MSAs.” If the account itself is not at fault – which can be maddening, as I’ve learned on a couple of occasions — deeper investigation into policies, security settings, and user profiles may be warranted.
Warning! This stuff can get hairy for those who are unfamiliar with such analysis and troubleshooting. Best to make an image backup (and be sure it’s easy to restore) before changing things at this level…
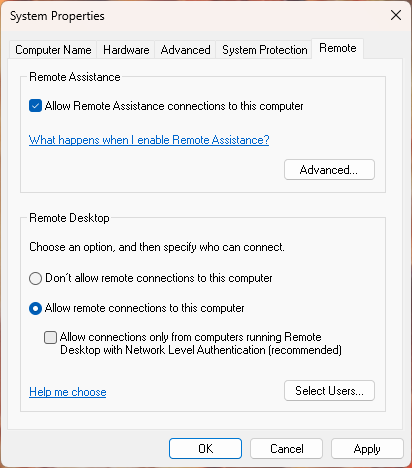
In digging into deeper causes, I’ve seen that Network-Level Authentication requirements (see next screenshot) can sometimes pose problems with RDP access.
Interestingly, this setting is still accessible only through Control Panel > System Properties on the Remote tab. If an MSA does not meet specific security requirements (for example, 2-factor authentication, aka 2FA – such as entering a 6-digit code sent via SMS to a phone number or to the email address associated with the account), RDP may refuse to establish a remote connection.
Other issues that can stymie remote access for MSAs include account restrictions or conditional access policies, where access conditions must be met or remote devices must jump various hurdles (such as passing health or security checks).
In some cases, the OS itself may get in the way. If the user profile for the MSA used for remote login is corrupt, RDP authentication may fail. Similar issues may occur because of software conflicts or updates, as when recent Cumulative Updates or third-party security tools interfere with proper handling of MSA logins.
I’ve seen this happen repeatedly with CUs and new version Insider Preview builds in all channels (Release Preview, Beta, Dev, and Canary).
MS is usually pretty fast about fixing such issues with new updates or versions.
Because remote access demands a working, trouble-free network connection, underlying network infrastructure elements – such as firewalls, port restrictions, or network segmentation – can prevent RDP from authenticating an MSA successfully.
It may be able to recognize the account, but something is preventing it from connecting the remote access client to the remote access host. Go figure!
What to do when Microsoft account authentication fails when using RDP?
When MSA authentication fails, my favorite workaround is to create a local administrator account on the target machine (for example, LocalOnly). Then, I’ll use those credentials for RDP access instead. While this method may limit access to certain user-specific files or settings tied to the MSA profile, it often enables a working RDP connection. The next screenshot shows the results of running various simple commands or checking environment variables, when logged into a local admin account via RDP.
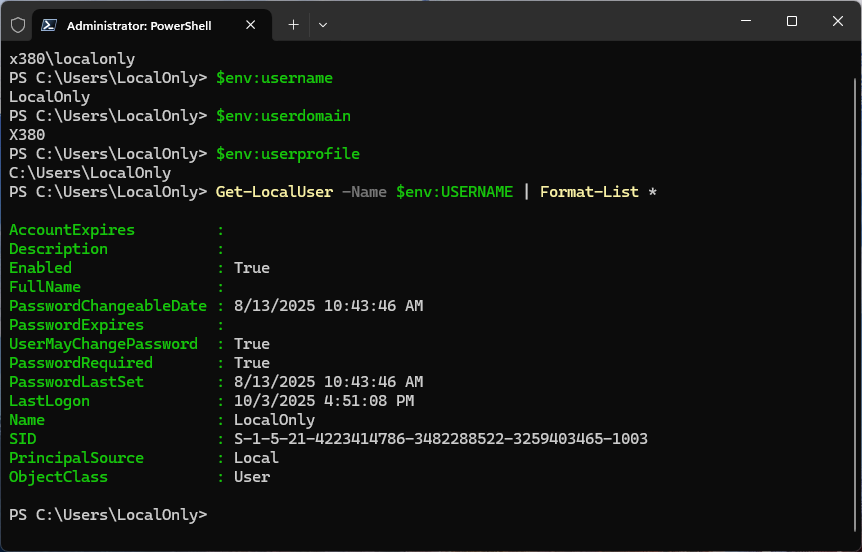
Some RDP login problems will provoke error messages that login credentials don’t work, or that report “LSA cannot be contacted” (LSA = Local Security Authority). When such things occur, users should also check recent Windows updates, review security software logs, and consulting network policies if those issues persist in the face of other fixes already mentioned in this story.
Here on my local network, I have 9 PCs into which I establish remote sessions. Of those machines right now, 7 work with an MSA, and 2 require a local account to obtain a working connection. Affected Windows versions include 24H2 and 25H2, mostly for Insider Previews in the Beta or Canary channels. When MS warns of potential stability and access issues with Insider Previews, methinks that RDP access via MSA is in that mix!
Indeed, as Microsoft continues to enhance security and integrate more cloud-based identity features into Windows 11, occasional incompatibilities like RDP access gotchas are likely to resurface.
Staying current with system updates and maintaining good configuration hygiene can help reduce the frequency and impact of these login challenges. For me, the local admin account approach remains a tried and tested workaround when MSA logins won’t work in Remote Desktop Connection.