Today, McAfee has announced that it has discovered a new vulnerability in Windows 10’s Cortana digital assistant which could be used to manipulate locked systems with physical access. It’s worth noting that the two new flaws have been addressed as part of Microsoft’s August update for Windows 10.
The vulnerability was discovered by McAfee Labs Advanced Threat Research team and the researchers responsible disclosed it with Microsoft which addressed the vulnerabilities in today’s patch.
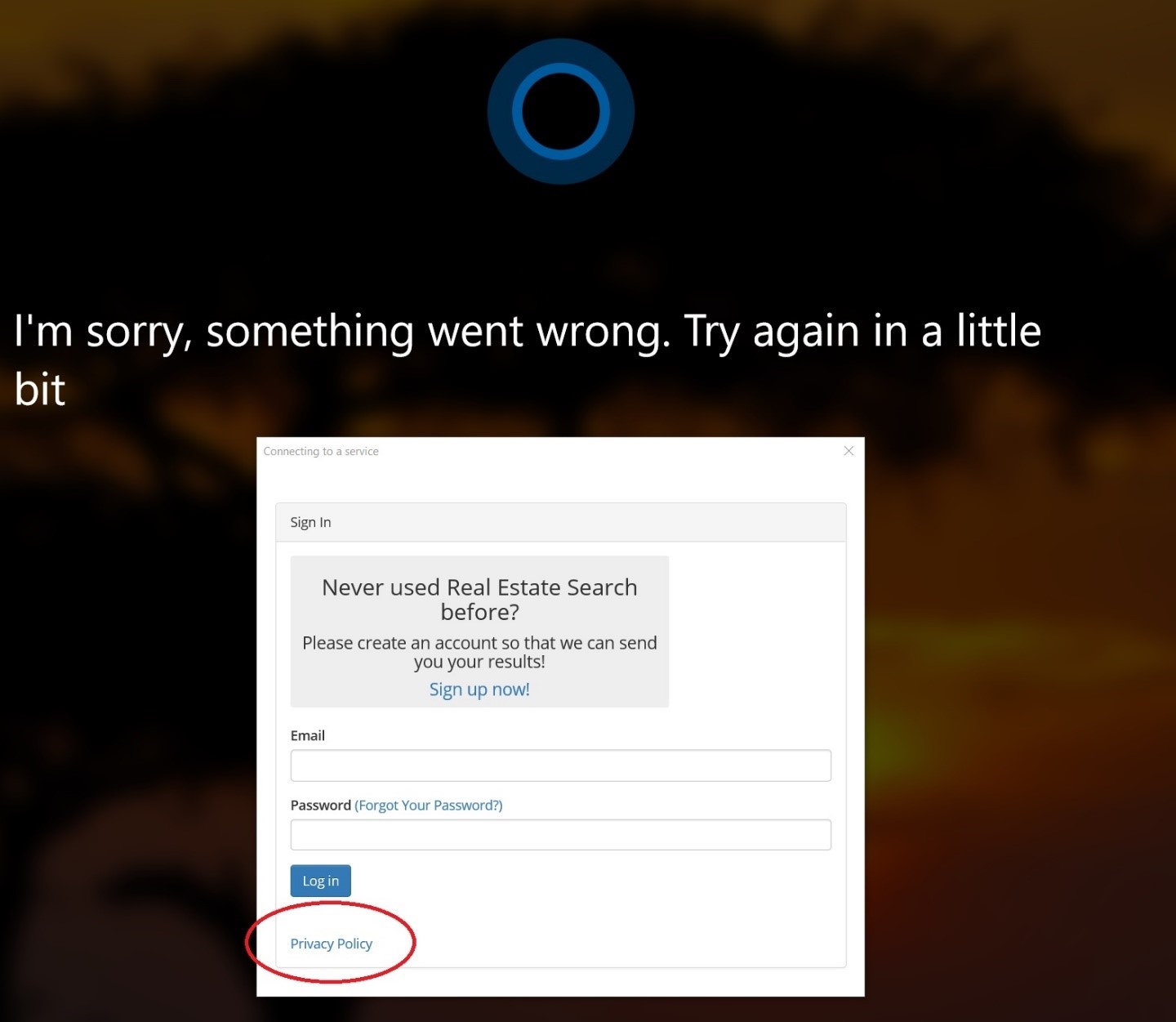
The company says that the locked Windows 10 devices with Cortana could allow an attacker with physical access to do two kinds of unauthorized browsing on the unpatched systems.
The vulnerabilities could allow the attackers:
- The attacker can force Microsoft Edge to navigate to an attacker-controlled URL.
- The attacker can use a limited version of Internet Explorer 11 using the saved credentials of the victim.
“In the first scenario, a Cortana privilege escalation leads to forced navigation on a lock screen. The vulnerability does not allow an attacker to unlock the device, but it does allow someone with physical access to force Edge to navigate to a page of the attacker’s choosing while the device is still locked. This is not a case of BadUSB, man in the middle, or rogue Wi-Fi, just simple voice commands and interacting with the device’s touchscreen or mouse,” researchers Cedric Cochin and Steve Povolny explains in a blog post.
Some additional discoveries by McAfee being addressed in the latest set of Patch Tuesday updates include:
- McAfee researchers discovered that Cortana can be forced to open an attacked-controlled page while in a locked state. One way bad actors can take advantage of this vulnerability is to manipulate Wikipedia pages (which Cortana frequently references while in locked mode as a “trusted site”) to contain malicious links and information.
- Researchers also discovered that attackers can access and navigate Internet Explorer through the Internet Explorer engine and not the full browser, though both JavaScript and cookies are enabled. Using this method, while the device is still locked attackers would be able to post comments on a public forum from another user’s device or impersonate the user thanks to its cached credentials.