If you deleted the “inetpub” folder, which was created after Windows April 2025 Updates, you need to immediately bring it back, or your system will remain vulnerable to potential security threats. Microsoft told Windows Latest that the folder can be restored when you turn on the IIS service, or you can also use a new PowerShell script released on May 28.
For those unaware, Windows 11 24H2 and other older versions of Windows, including Windows 10, created a folder called “inetpub” after the April 2025 Updates. This empty folder is typically associated with Internet Information Services (IIS), which is a native Windows service that allows developers to host websites or apps on Windows 11.
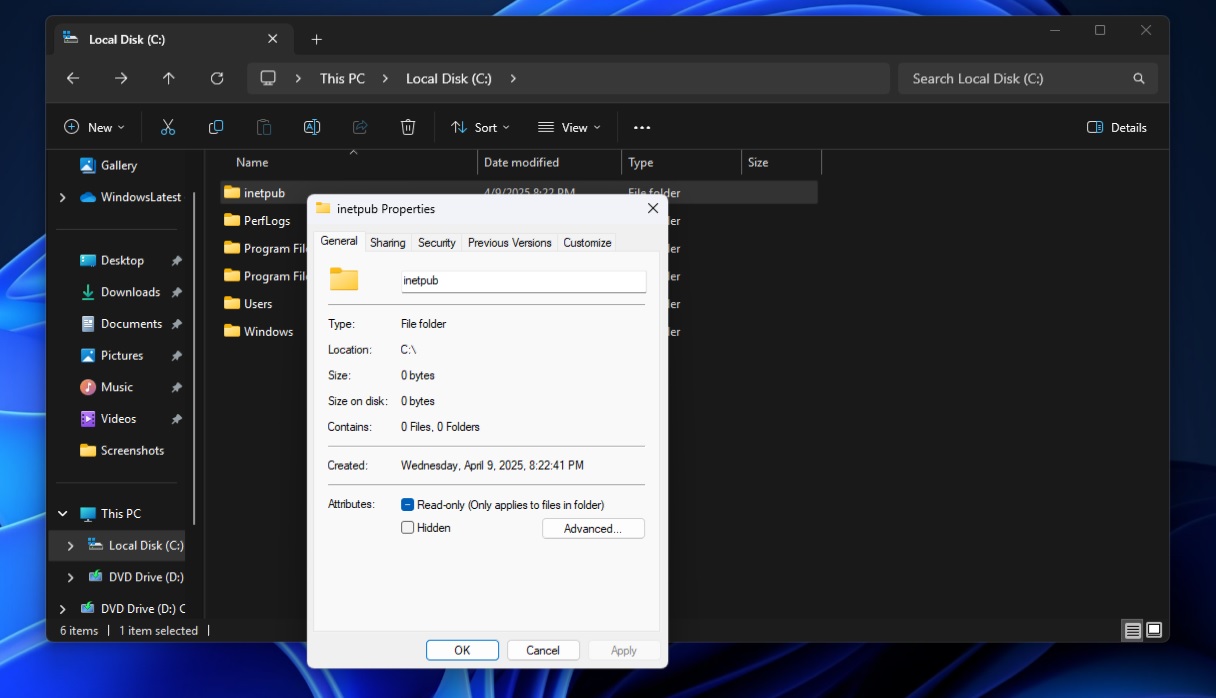
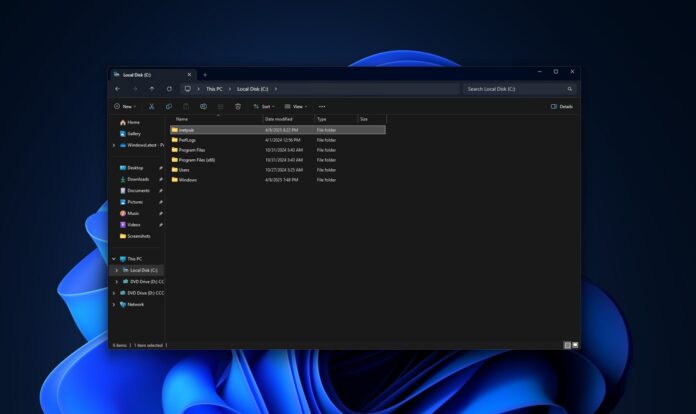
In case of Windows 11, Microsoft created the directory (C:\inetpub\) with KB5055523 or newer, but as you can see in the above screenshot, it doesn’t contain anything and the properties show the folder has zero bytes of data.
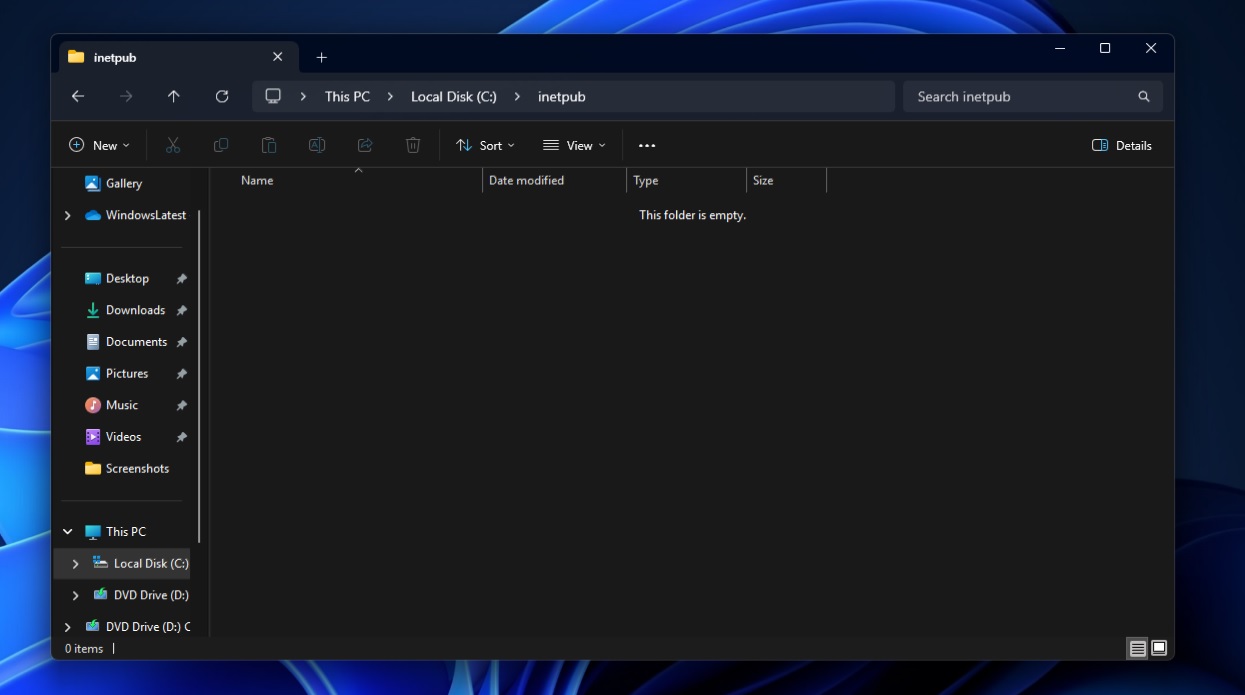
When I checked the settings, IIS was also not turned on. Unfortunately, since Microsoft never acknowledged that “inetpub” is an intentional change in its release notes, some of us assumed that it’s a bug with the cumulative update and deleted the folder.
Others deleted it because they were sceptical of Microsoft’s practices, especially creating a folder to patch a bug in the OS when the folder can be easily deleted, which makes us wonder what kind of patch is this?
Microsoft later updated its documentation and told Windows Latest that “inetpub” folder is created as part of a security patch for CVE-2025-21204, and it doesn’t matter whether IIS is turned on or not. It’ll show up, and you’re not supposed to delete it, and if you deleted it, please bring it back, according to Microsoft.
“The CVE-2025-21204 security flaw is caused by an improper link resolution issue before file access (‘link following’) in the Windows Update Stack which likely means that, on unpatched devices, Windows Update may follow symbolic links in a way that can let local attackers trick the system into accessing or modifying unintended files or folders,” Microsoft noted in a document.
Previously, Microsoft told Windows Latest that the “inetpub” folder can be recreated with the same level of security by turning on Internet Information Services (IIS) from Control Panel > Programs > Programs & Features > Turn Windows features on or off.
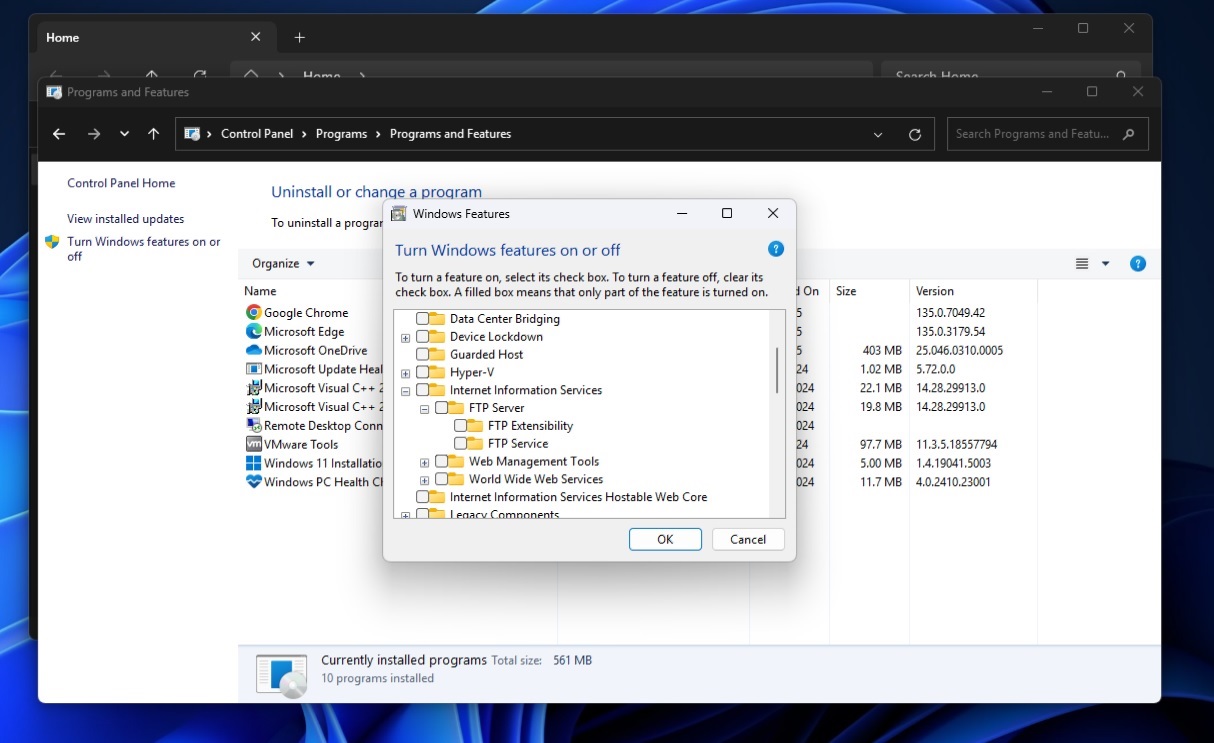
However, that’s something most people don’t want to do because IIS also creates additional folders, which are not required unless you’re a developer.
Windows Latest today spotted that there’s a new PowerShell script that recreates the folder, and you don’t have to turn on IIS anymore.
Microsoft published the script on May 28, and here’s how to use it.
How to use PowerShell script to restore “inetpub” and patch CVE-2025-21204?
- Run PowerShell “as Administrator.” You can’t do that using a non-admin account because we’re trying to change folder ACLs and install modules. These require admin privileges.
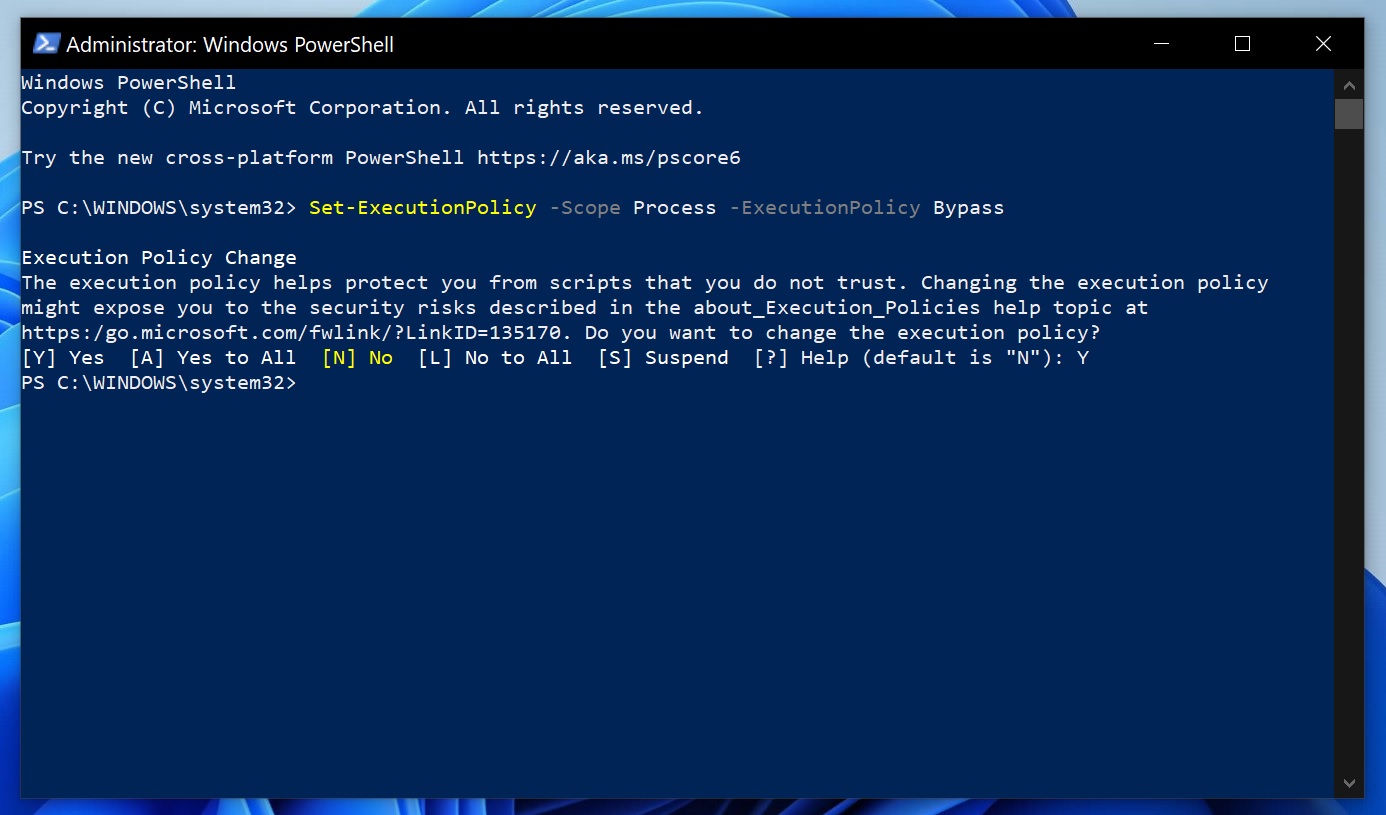
- In PowerShell, first allow signed scripts and modules from Microsoft’s PowerShell Gallery with the following command: Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
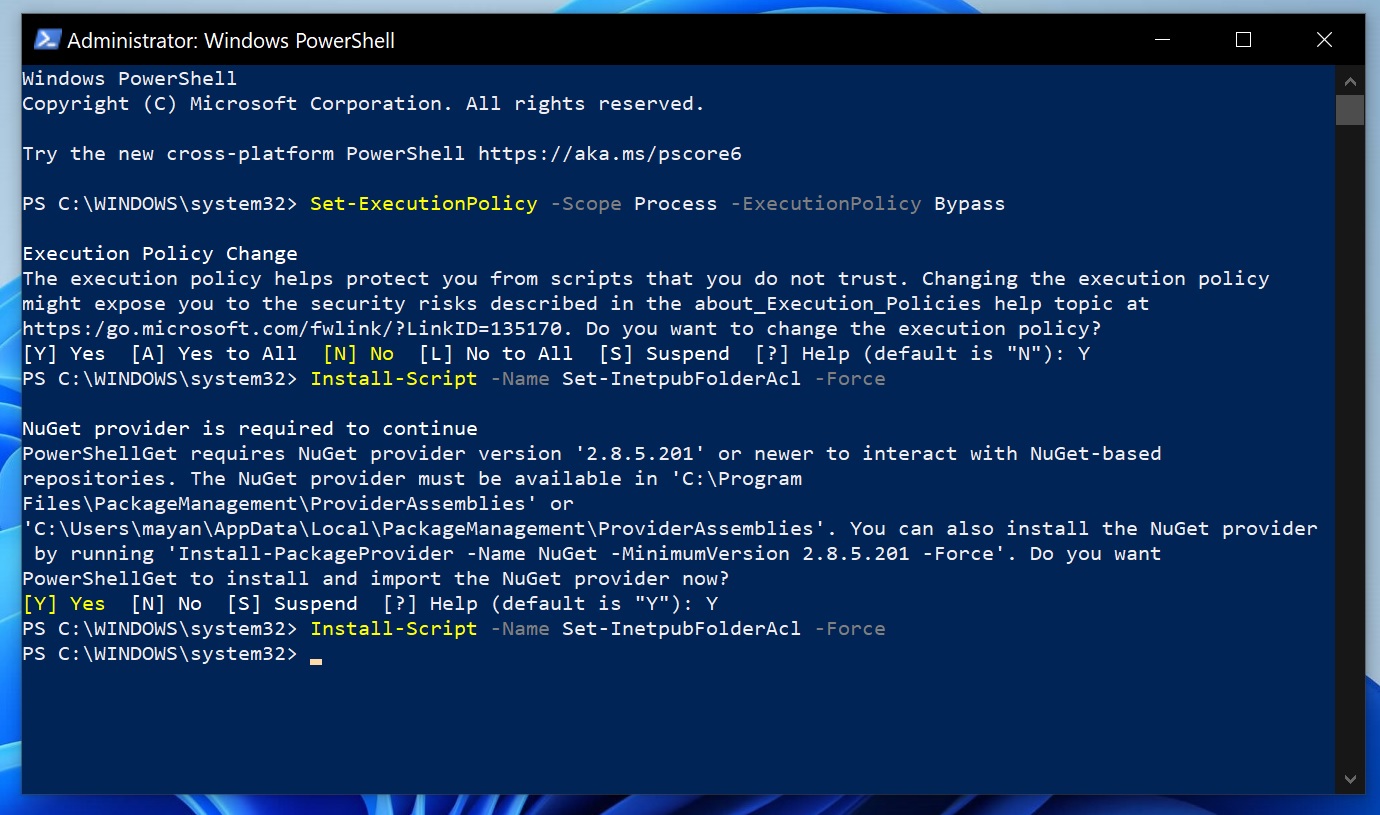
- To download the script from the PowerShell gallery, run the command: Install-Script -Name Set-InetpubFolderAcl -Force
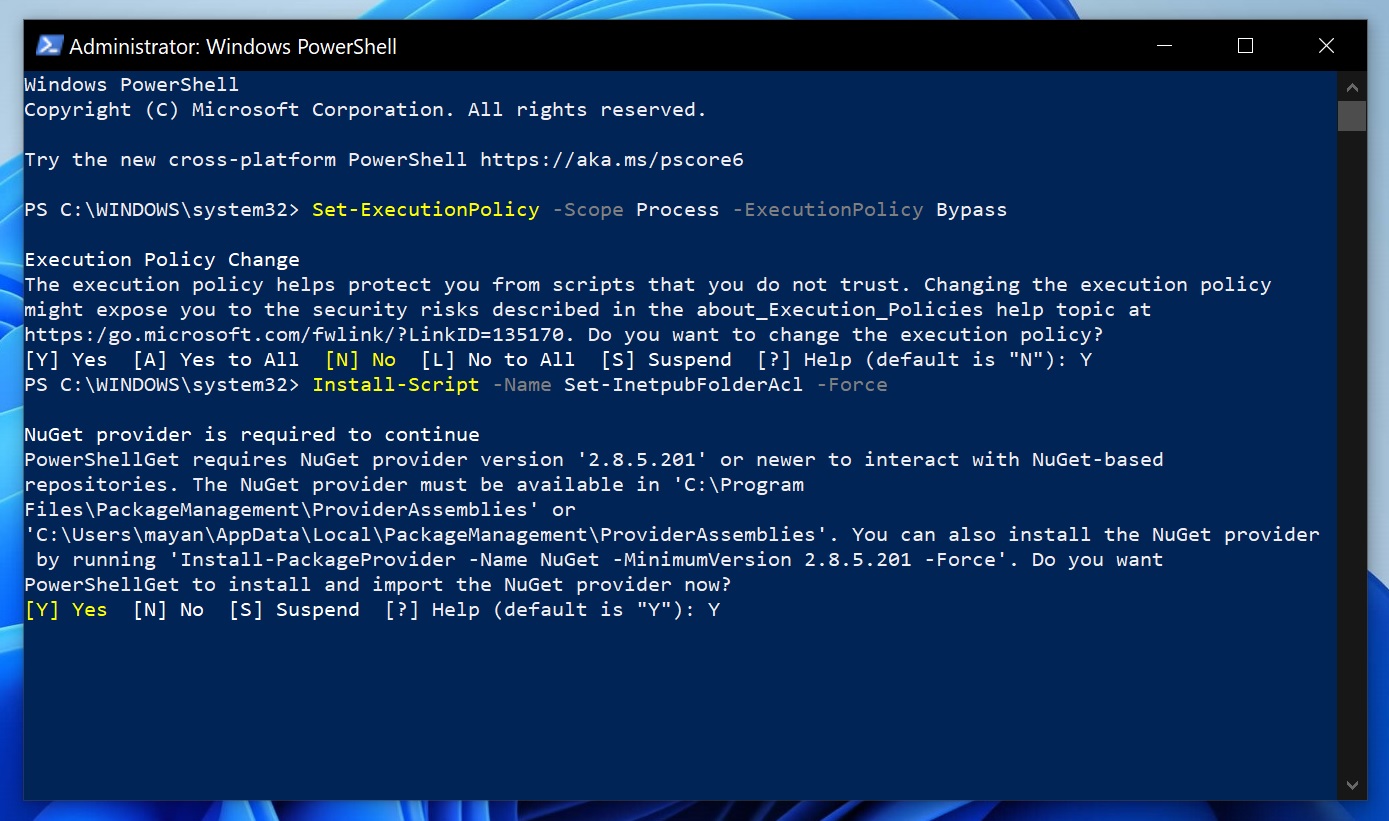
- In some cases (like mine), you’ll be asked to install “NuGet Provider” when it’s not present. Simply respond with “Y” to proceed, and run the above “install-script” again.
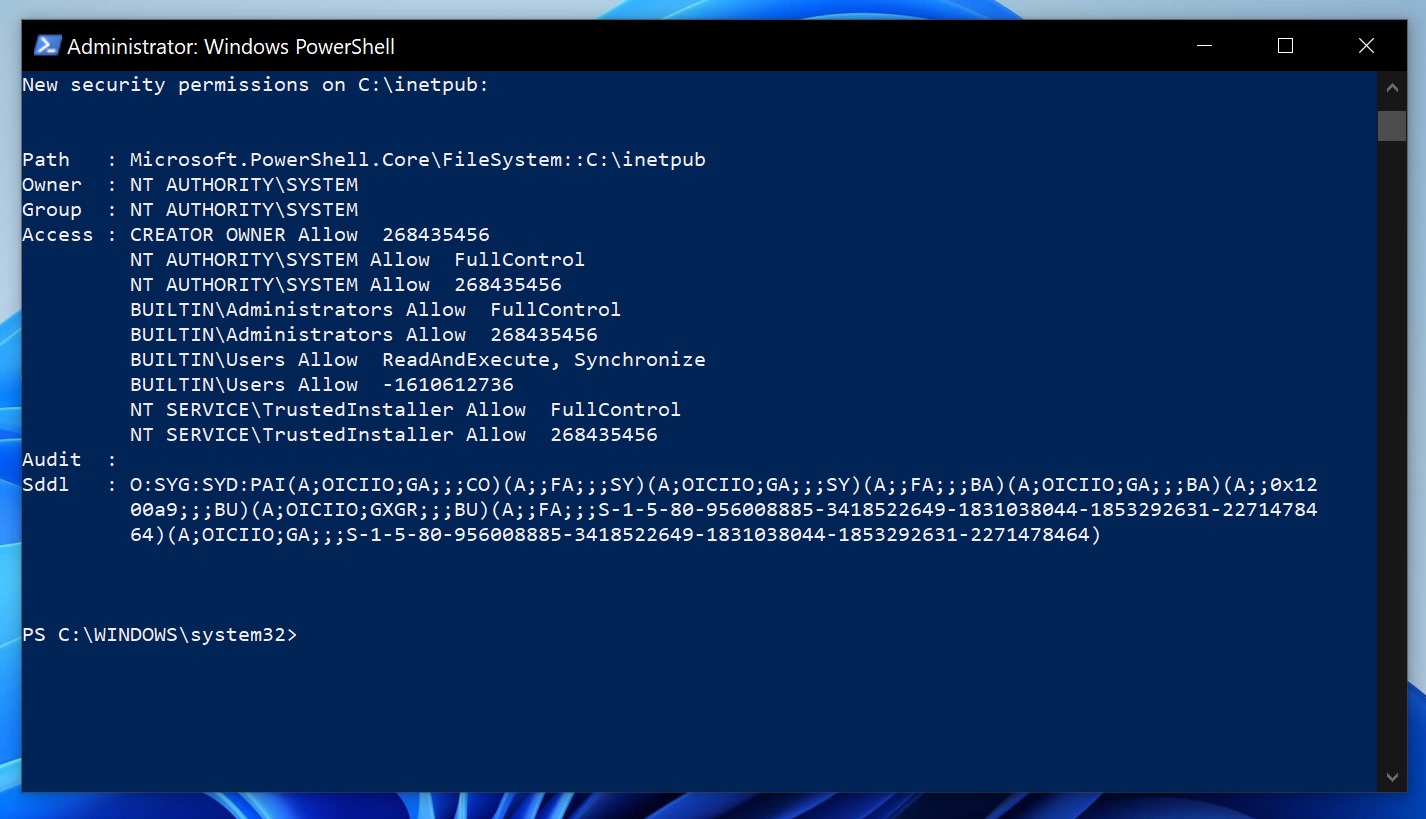
- Run “Set-InetpubFolderAcl” to apply the fix and create the folder. But if you get an error that says “command not found” error, run it by full path:
& "C:\Program Files\WindowsPowerShell\Scripts\Set-InetpubFolderAcl.ps1"
How does Install-Script command works?
Should you really bother with “inetpub”? I’d recommend that you do. It should be present on your system. As per Microsoft, without the folder and its correct ACLs (Access Control Lists), you remain exposed to potential privilege escalation or unauthorised access.
By running the Set-InetpubFolderAcl.ps1 script I highlighted, you’re recreating the folder and applying the proper IIS-style permissions so that the April 2025 Update fix for CVE-2025-21204 actually takes effect.
Got questions? Let me know in the comments below.